Apr 26, 2023
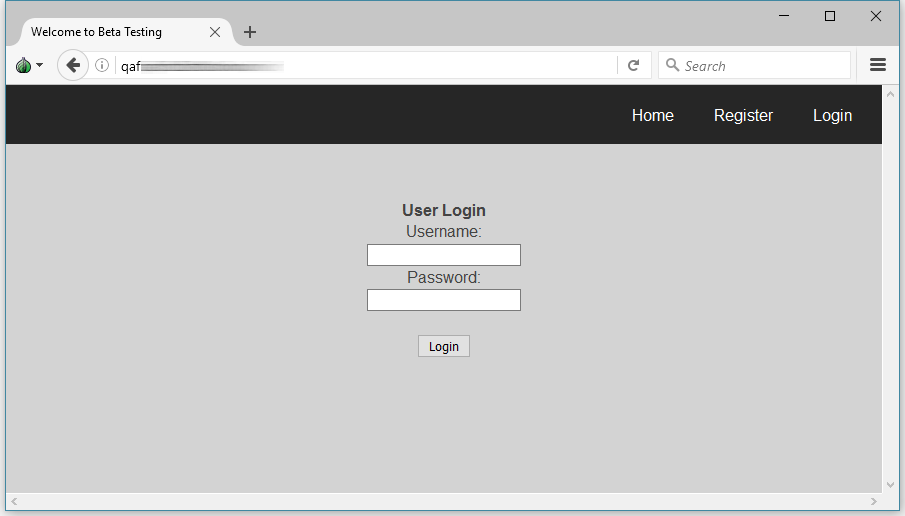
Accessing the Dark Web: A Guide to Login
Just like in the physical world, the cost of purchasing stolen data on the dark web varies depending on market conditions, which means that the price of your online browsing history may also be subject to change.
DuckDuckGo is a well-known private search engine that is widely used. By adhering to the aforementioned guidelines, coupled with the use of a trusted VPN and the Tor browser, it is possible to gain entry to dark web pages without endangering oneself. It is recommended to employ a dependable password manager for added security.
When you finish browsing, certain cookies are automatically cleared.
Accessing the Dark Web: A Guide to Logging In
In contrast to other search engines, there is no gathering or exchanging of personal information. Although the Tor browser is the most popular way to enter the dark web, other communication platforms like Signal can also be utilized. The dark web is uncontrolled and inhabited by numerous dubious individuals.
Encrypting your traffic is a crucial step in ensuring your online activity remains private and secure, particularly when accessing the dark web. However, managing multiple login details for various dark web sites can be a daunting task. Reusing passwords across different platforms poses a grave security threat that must be avoided at all costs.
The dark web is utilized by whistleblowers, journalists, and political dissidents as a platform to disseminate information that might otherwise be censored or suppressed. It is crucial to adhere to additional security measures when accessing the dark web, such as employing the Tor browser and steering clear of dubious links and downloads. The Cybercrime-as-a-Service (CaaS) gig economy is the primary catalyst for economic expansion on the dark web, and its size increases annually.
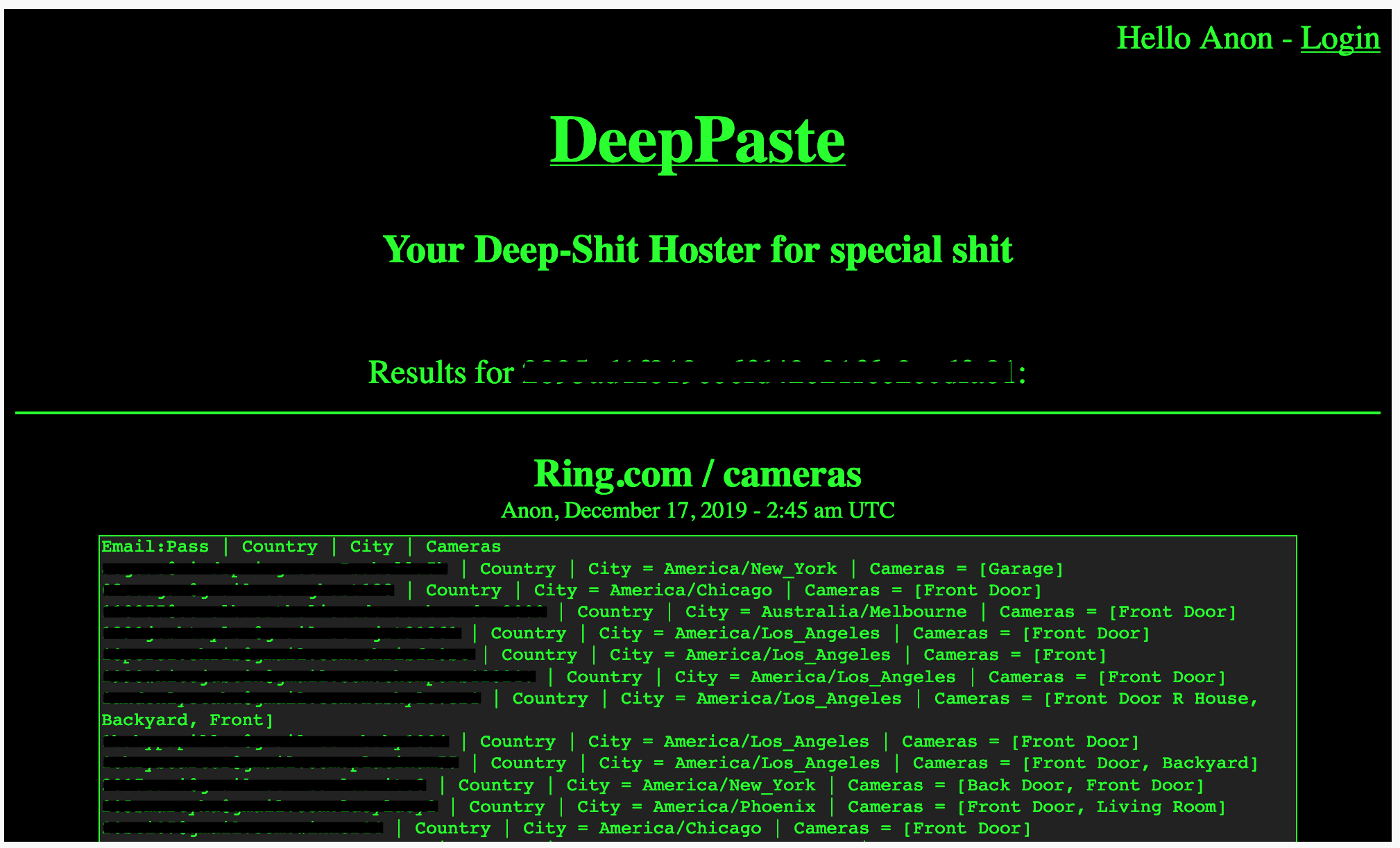
Around 90% of the messages on well-liked dark web discussion boards are believed to come from individuals seeking to employ a cybercriminal's services. Those who have the correct proxy can access these websites, while others are barred. These criminal activities generally involve the theft of confidential information from unsuspecting victims, with threats to make it public on the dark web if the ransom is not paid.
Secrets to Accessing the Dark Web
Accessing the dark web through Tor is possible in two methods: Bridge and Relay. A bridge is a server within the Tor network that offers access to blocked clients, often working together with pluggable transports, and is registered with the bridge authority. Meanwhile, SearX is a search engine specifically built for the dark web, allowing users to conduct extensive searches. On the other hand, a relay is a server that is publicly listed in the Tor network and is responsible for forwarding traffic on behalf of clients, registering itself with the directory authorities.
It is important to note that the dark web login process should be approached with caution, as law enforcement agencies may be conducting surveillance and participation in illegal activities or visiting specific websites may lead to criminal charges. There are various platforms for whistleblowing, such as a dark web adaptation of Wikileaks. It is essential to be vigilant against fraudulent schemes.
According to him, the dark web login scene is highly dynamic, with sites frequently changing their addresses to evade DDoS attacks.
Despite its ominous name, not all of the dark web is utilized for unlawful activities. A direct link to access it is https/. One factor that sets it apart is its unique naming system.
Can accessing the dark web be considered illegal? It provides access to various illicit activities such as DDoS attacks, botnets, remote access Trojans (RATs), keyloggers, and exploits. The dark web also offers services for espionage, customization, and targeting. Based on the 2021 Dark Web Price Index by Privacy Affair, here are the prevailing rates for some of the frequently traded data and services: cloned credit cards with PINs range from 25 to 35 credit cards.
The clear web, which is commonly referred to as a standard web browser, only provides access to a small fraction of the internet.
Accessing the Dark Web on Your iPhone: A Step-by-Step Guide
Logging in to the dark web might appear to be a straightforward task given the bustling marketplace and activity that surrounds it. However, this perception is often exaggerated and overhyped. The reality is that navigating the dark web is not as simple as it seems. Although it's true that illegal items such as drugs, fake passports, and weapons can be purchased, the media tends to overemphasize this aspect of the dark web.
It is important to remember that the dark web is unregulated, meaning that there is no assurance that the websites you dark web login access are secure or lawful.
To secure your device against possible dangers you might come across while accessing the dark web, it's recommended to follow these guidelines. Additionally, purchasing login details like usernames and passwords is an option available to you. Follow these safety tips to navigate the dark web with peace of mind.
When you utilize websites or online marketplaces that enable unlawful activities, you may unintentionally endorse these illicit actions and add to the damage that they create. As previously stated, it is crucial to make use of a VPN and a browser such as Tor Browser when logging into the dark web.
For those in search of a login page for the dark web, try out Duck Duck as a search engine. Check out the Hidden Wiki, which is a modified version of Wikipedia that provides an extensive list of links to help navigate through the dark web.
Explore further
Distributed by livvyshea837, LLC.