Apr 26, 2023
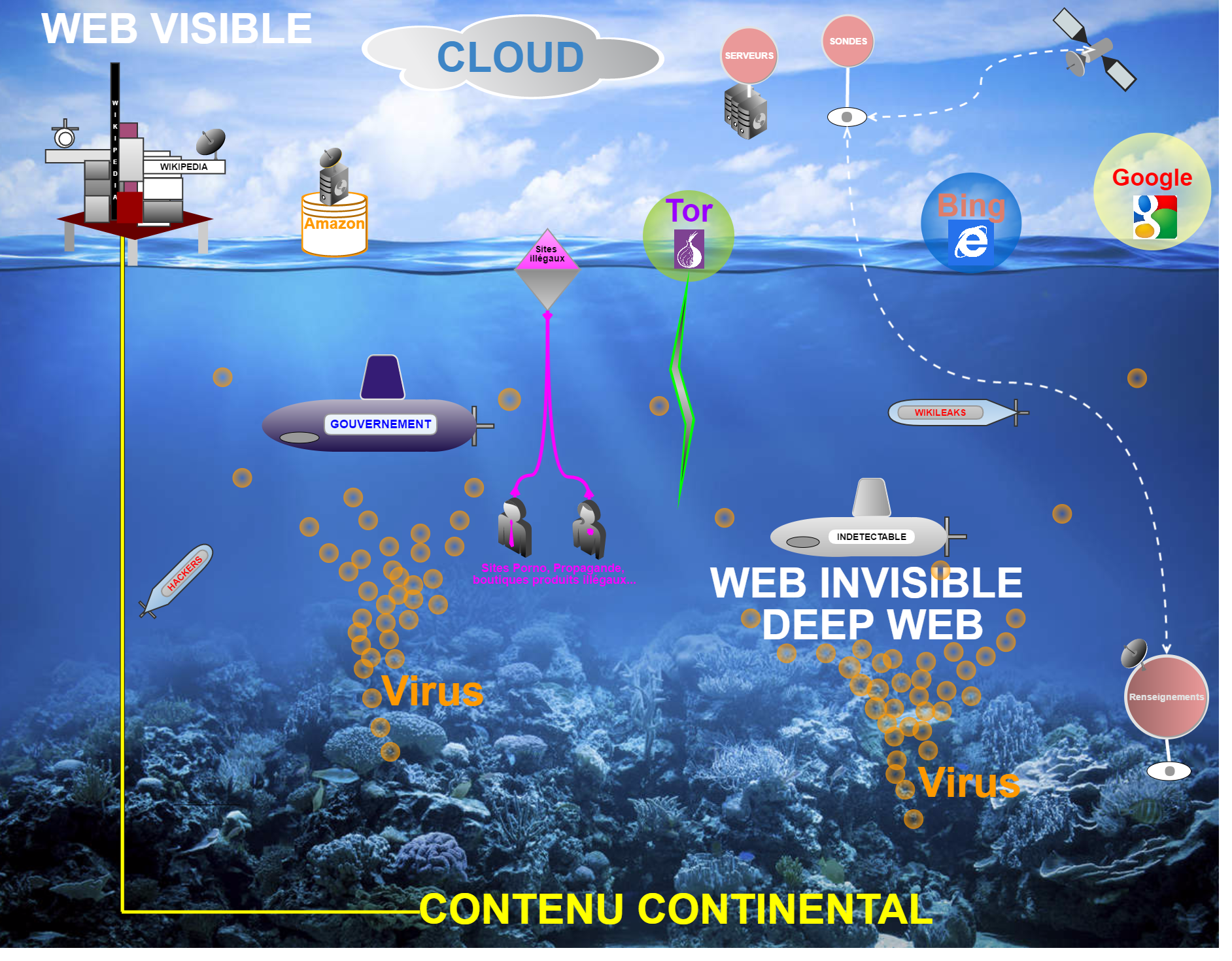
Keeping Tabs on the Dark Web: The Importance of Monitoring

Rewritten:
Benefits: Offers access to information from the Deep and Dark Web, with added reports on threat patterns. Also, it tracks any references made to client-specific
data on hacker forums and can uncover previously unknown data theft.
Drawbacks: However, users still need to devise a plan to manage any data breaches that are exposed. Additionally, the system may produce many false-positives due to the high volume of legitimate traffic on the Tor network.
Instead of solely concentrating on safeguarding accounts, dark web monitoring services aim to safeguard not only the reputation but also the confidential information of organizations. Equipped with the ability to detect data security breaches, these services scour the hidden corners of the internet to identify malicious data repositories that contain sensitive data pertaining to both companies and individuals. Network administrators can benefit from the top-notch dark web monitoring tools available in the market. To select the most suitable dark web intel system, we evaluated various tools based on their data-gathering capabilities, among other criteria.
Our team has compiled a comprehensive roster of top-notch dark web monitoring services (opens in new tab) available today. One of the areas where they prove to be particularly useful is in keeping a watchful eye on Gmail (opens in new tab) accounts for any suspicious activity. It's worth noting that experts in the fields of journalism and cybersecurity often use the term "dark web" to refer to illegal online activities in general.
Dark web monitoring services offer continuous updates through repetitive scans, providing access to disclosed information on a dashboard for subscribing companies that the data concerns.
An illustration of a Dark web monitoring service is the SearchLight, which scans for company procedural documents, site plans, and internal memos that may have been leaked on other sites that are notorious for dealing in corporate information unlawfully. By keeping an eye on these trusted partners, you can enhance your supply chain security and avert cross-domain attacks that may bypass your current security measures.
Keeping an Eye on the Shadows: Dark Web Monitoring Services
Dark web monitoring services are becoming increasingly popular among companies in order to protect their assets and personal information from cyber criminals. One example is CrowdStrike Falcon Intelligence Recon, a research service that specifically searches Dark Web sources for any mentions of a company's assets. Additionally, RiskPrime offers monitoring for personally identifiable information (PII) and tracks compromised VIP accounts, while also performing reputation monitoring and phishing detection to prevent any potential cyber attacks.
Although there are search engines for the dark web monitoring services dark web, none of them come close to the vastness of Google. These dark web monitoring services solely focus on detecting data breaches associated with email addresses.
Dark web monitoring services are becoming increasingly popular as businesses seek to protect their sensitive data from cyber threats. WhatsUp Gold's Tor detector is a standout feature that sets it apart from other network threat detection systems. By providing actionable intelligence, the software allows businesses to prioritize their response based on the level of risk and minimize response time, facilitating quick and efficient remediation.
These monitoring services cover a range of sites, including social media channels, shopping platforms, and personal blogs, that are indexed on public search engines like Google, Bing, and DuckDuckGo. By monitoring these sites, businesses can identify potential threats and take action before any damage is done.
Registering for an account is not a requirement when utilizing dark web monitoring services. Simply providing an email address in the designated input field on the service's homepage is sufficient.
Safeguarding Your Online Identity: Dark Web Monitoring with Onions Links
Continuous dark web monitoring services are conducted by automated web bots that operate 24/7. Palo Alto Networks conducts comprehensive searches across data repositories on both the open internet and the dark web. The collected data is then correlated and contextualized using information obtained from the global footprint of devices and services offered by the vendors.
Monitoring services for the dark web are limited in their ability to scan the entire network, which is an impossible task. Marriott Starwood, for instance, took almost four years to identify that its reservation system had been breached, and then waited for nearly three months before informing its 500 million customers who were affected. The advantages of these services include the use of password managers and data storage protection. However, it's important to note that these services do not offer remediation options once an account has been compromised.
IntSights offers dark web monitoring services that enable you to stay vigilant and take preemptive measures against potential threats. With their product, you can monitor ongoing discussions in the dark web that pertain to your company's brands or domains. By doing so, you can respond proactively rather than reactively when a threat arises. Instead of relying solely on clearnet sources, you can leverage specialized tools and services that scan the dark web for potential risks.
If your personal financial information such as bank account or credit card data is compromised, it is advisable to inform your financial institution immediately to prevent any unauthorized transactions. Moreover, it is recommended to secure your credit report and prevent cybercriminals from opening new credit lines using your identity.
One of the available enhancements is the Network Traffic Analyzer, which offers a 15-day trial. Additionally, there is a complimentary scan of Dark Web activity related to email addresses.
With the rise of the covid-19 pandemic, a large number of individuals have shifted towards online platforms for various activities such as work, studies, shopping, communication, and entertainment. Consequently, people have created more online accounts than ever before, making them vulnerable to cyber attacks. Cybercriminals are targeting popular apps and websites, and it has become imperative to monitor the dark web for any suspicious activities that may put personal information at risk.
Keeping an Eye on the Dark Web: Onion Links Monitoring Services
Subscribe to the TechRadar Pro newsletter for the latest news, opinions, features, and advice your company needs to thrive. This service is based in the cloud and allows access to the Dashlane customer dashboard via a browser or mobile app. Any potential hazards are flagged and an alert is sent to the network administrator for prompt action.
Dark web monitoring services are essential for individuals and businesses who want to keep their sensitive information safe from cybercriminals lurking on the dark access the dark web web. It is impossible to completely erase any data that has been leaked on the dark web, but with the help of monitoring services, you can stay informed about any potential breaches and take action to protect your data. One such service is WhatsUp Gold, which is a network traffic monitor that has the capability to detect traffic coming from the Tor network. This can be a useful tool in identifying any suspicious activity and preventing any unauthorized access to your sensitive information.
Dark web monitoring services are essential for security professionals to keep themselves informed about the latest attack methods. This allows them to adapt their defenses and educate users on the most effective practices. Hackers often use Tor to conceal their origins and movements on the internet, which is where monitoring services come in handy. They can scan incoming traffic and emails for any signs of malicious activity, using known sources as a guide to identify any potential threats.
Dark web monitoring services are not inherently illegal. These services track well-known cybercriminal forums and marketplaces where data breaches are often sold. Users can input personal information such as names, social security numbers, or email addresses to search through sources on the dark web. This includes marketplaces, social media sites, and forums to locate instances of their information being sold or publicly shared on free lists.
Explore further
Distributed by ALWASLUAE, LLC.